Wi-Fi Security
Posted
on
in
Security
• 780 words
• 4 minute read
Tags:
wifi
The Evolution of Wi-Fi Security: A Tale of Protection and Progress In the early days of wireless networking, the digital world was like the Wild West – open, exciting, but also dangerous. When Wi-Fi first emerged in the late 1990s, data traveled through the air unprotected, visible to anyone with the right equipment. It was like shouting your secrets in a crowded room and hoping no one was listening.
Chapter 1: WEP - The First Shield
Recognizing the need for privacy, the creators of Wi-Fi introduced Wired Equivalent Privacy (WEP) in 1999. WEP was like a simple lock on a door – it kept honest people out but wasn’t much of a challenge for determined intruders. Its goal was noble: to make wireless networks as secure as wired ones. However, WEP had a fatal flaw. Its encryption keys were short and static, like using the same simple password for years. Hackers soon found they could crack WEP encryption in minutes, sometimes even seconds. It was clear that a stronger shield was needed.
Chapter 2: WPA - A Stronger Fortress
In 2003, Wi-Fi Protected Access (WPA) arrived to address WEP’s shortcomings. WPA was like upgrading from a simple lock to a more complex security system. It introduced TKIP (Temporal Key Integrity Protocol), which dynamically changed encryption keys. This was akin to changing your password frequently, making it much harder for eavesdroppers to crack the code. WPA also brought improved user authentication, ensuring that only authorized users could access the network. However, while stronger than WEP, WPA still had vulnerabilities, particularly in its use of TKIP, which was based on the same underlying system as WEP.
Chapter 3: WPA2 - The Iron Curtain
Just a year later, in 2004, WPA2 emerged as the new standard. This was like fortifying your castle with iron walls and a moat. WPA2 introduced the use of the Advanced Encryption Standard (AES), a much more robust encryption method. It also employed CCMP (Counter Mode Cipher Block Chaining Message Authentication Code Protocol) for authentication, significantly enhancing security. WPA2 was so strong that it became the Wi-Fi security standard for over a decade.
However, even iron can have weak points. In 2017, the KRACK vulnerability was discovered. While not a flaw in the encryption itself, KRACK allowed attackers to potentially read information that users assumed was safely encrypted.
Chapter 4: WPA3 - The Enchanted Fortress
Responding to evolving threats and the KRACK vulnerability, WPA3 was introduced in 2018. Think of WPA3 as upgrading to a high-tech security system. It brought several key improvements:
Stronger encryption. Protection against offline dictionary attacks, making it much harder for attackers to guess passwords. WPA3 also addressed the KRACK vulnerability, closing that secret tunnel into the network.
From ‘Connecting…’ to Connected: The WPA Protocol in Action
The 4 - Way Handshake
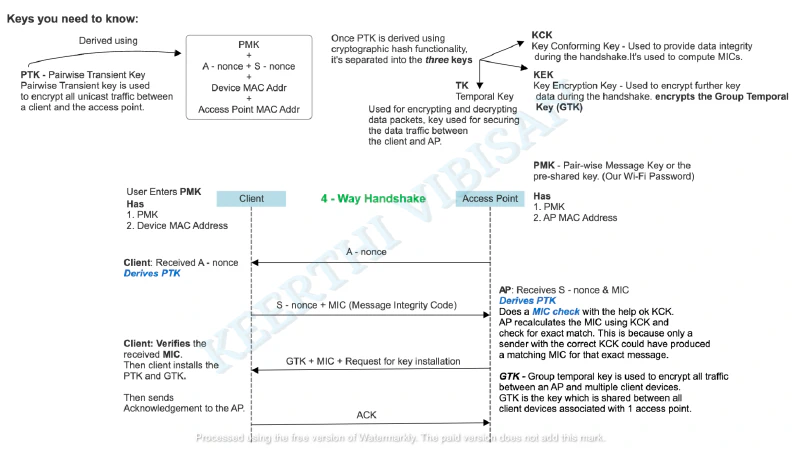
NOTE: For details on all keys (PTK, KCK, KEK, TK, etc.) involved in the process, refer to the image.
- Initial Message (from AP to Client): The Access Point (AP) sends a random number called A - Nonce (Authenticator Nonce) to the client. This message is unencrypted and has no integrity check. (If some mess happens here the handshake fails)
- Client Response: The client receives the A - Nonce and generates its own random number called S - Nonce. Using the A - Nonce, S - Nonce, MAC Addresses and the Pre-Shared Key (PSK the Wi-Fi password), the client generates the Pairwise Transient Key (PTK). The client sends the S - Nonce to the AP, along with a Message Integrity Code (MIC) generated using KCK part of the PTK. Note: Here the PTK or the KCK is not sent to AP from the client.
- AP Confirmation: The AP receives the S - Nonce and can now also generate the PTK. The AP verifies the MIC to ensure the client has the correct PSK. If verified, the AP sends the Group Temporal Key (GTK) to the client, encrypted with KEK part of PTK. This message also includes another MIC for integrity checking.
- Client Acknowledgment: The client verifies the MIC from the AP’s message. If correct, it sends an acknowledgment to the AP. At this point, both the client and AP have verified each other and established the necessary keys for secure communication.
Wi-Fi security may seem complex, but it’s essential for protecting our online activities. Every time we connect to a network, these hidden processes work to keep our data safe. Remember, a secure Wi-Fi connection starts with you – use strong passwords, keep your devices updated, and be cautious on public networks. The 4-way handshake and encryption protocols are doing their part behind the scenes, but your awareness is the first line of defence.