Posted
on
in
Security
• 373 words
• 2 minute read
Tags:
Security
The demo of this POC is deployed here feel free to check Device Auth
I believe the future of authentication lies in something we already carry everywhere with us, our mobile devices.
IAM is changing, Users no longer want to remember or enter complex passwords every time. Also the security team no longer trust the static passwords that can be stolen or phised.
So i think by turning devices into secure identity, we can make authentication user friendly and secure proof.
Why Passwords Are Fading Away
We’ve all seen it, the endless cycle of “Forgot Password?”, copy pasting OTPs and worrying about phishing emails. Passwords are not designed to scale for today’s digital world.
That’s where authentication is moving beyond passwords to modern and simpler approaches:
Biometrics: Fingerprint, Face ID
Passkeys: Secure replacements for passwords, powered by FIDO2/WebAuthn
Device-based trust: Where your device itself becomes a secure identity anchor
How Device Identity Works
So how do we make a device trustworthy? The answer lies in Cryptographic signature + certificate based verification.
So here each device generates its own private & public key pair. The public key is bound to the user and will be signed by the server as certificate, while the private key never leaves the device. Authentication requests are signed locally, only after the user confirms with fingerprint, Face ID, or an MPIN.
Here’s the flow
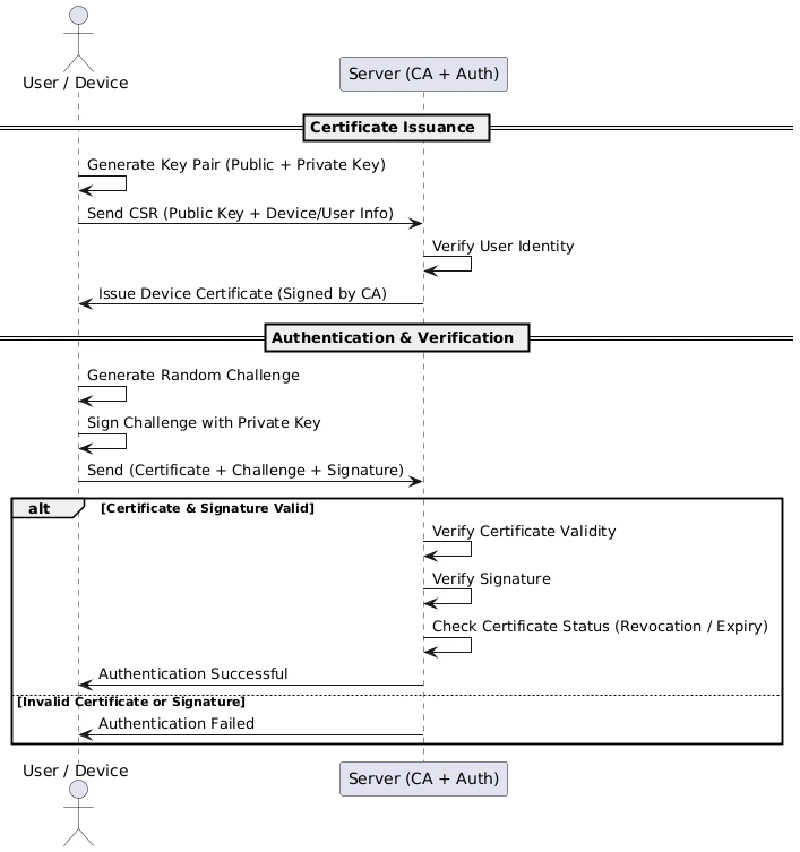
1. Device Registration
Device generates a private–public key pair.
Public key and user/device info are sent to the server.
Server verifies the user identity and issues a signed certificate.
Private key stays secure on the device, it never leaves.
2. Device Verification (Authentication)
The device generates a random challenge and signs it locally using its private key.
User verification happens locally (fingerprint, Face ID, MPIN).
Device sends the signed challenge + certificate to the server.
Server verifies the signature and certificate.
If valid, access is granted.
Conclusion
This is not a industry standard or finalized protocol. This is a POC I built from my own ideas. My goal was to explore how we can shift authentication toward device first approach.
While this is just an early step, I believe approaches like this can shape how Identity & Access Management evolves in the years ahead.
