Posted
on
in
Cryptography
• 798 words
• 4 minute read
Tags:
Cryptography
From the continuation of Cryptography Intro
Our Sensitive data's are by default in clear text, when they are stored in RAM or in transit, so anybody who can read RAM or Data packets can get our information, so it is our responsibility to secure it, we cannot stop any one from reading it, but we can make the data un-understandable using encryption techniques.
Encryption
Process of converting the plain text to cipher text (unreadable text).
These cipher texts can only be decoded by someone with the correct key or decryption method, so only authorized parties can decode/decrypt it.
Decryption
Process of converting the cipher text back into plain text.
Two Main Types of Encryption Techniques
- Symmetric Key - Same key is used for both encryption and decryption. (Public Key Alone)
- Asymmetric Key - A Pair of key is used here, Public Key to encrypt and a private key to decrypt.
Let’s look at Symmetric Key Encryption
Encrypt and Decrypt file using OpenSSL
- Generate a Symmentric key
openssl rand -hex 32
Output:
41113300689613875dea03bacb07262aecd6eeda2f0898fc84a856d47dc11e3f
- Generate Initialization Vector
openssl rand -hex 16
Output:
b234a59d0bf10a72962487613eedfe44
- Create a file to encrypt
echo "Thats Great Secret" > secret.txt
- View the contents of the file
cat secret.txt
Output:
Thats Great Secret
- Encrypt the file
openssl enc -aes-256-cbc \
-in secret.txt \
-out encrypted.txt \
-K 41113300689613875dea03bacb07262aecd6eeda2f0898fc84a856d47dc11e3f \
-iv b234a59d0bf10a72962487613eedfe44
- View the content of encrypted file
cat encrypted.txt
Output:
2?????>???ڱ2?8Ή?rVVG???%
- lets decrypt the file
openssl enc -d -aes-256-cbc \
-in encrypted.txt \
-out decrypted.txt \
-K 41113300689613875dea03bacb07262aecd6eeda2f0898fc84a856d47dc11e3f \
-iv b234a59d0bf10a72962487613eedfe44
- View contents of decrypted file
cat decrypted.txt
Output:
Thats Great Secret
So here you can see something like -aes-256-cbc, Where
- AES (Advanced Encryption Standard) is the encryption algorithm.
- 256 is the key size (in Bits).
- CBC (Cipher Block Chain) is the mode of encryption.
There are different types of symmetric key encryption algorithms
- AES (Advanced Encryption Standard)
- DES (Data Encryption Standard)
- 3DES (Triple DES)
- Blowfish
- Twofish
- RC4
- ChaCha20
But AES is the most popular and widely used one today because of its high security and speed. It is also optimized for both hardware and software applications use, which makes it a standard choice in encryption systems like HTTPS, VPNs and etc. Also AES is a Block Cipher type of Symmentric Key Encryption Algorithm.
- Stream Cipher type of encryption encrypts data one bit or byte at a time.
- Block Cipher is a type of encryption in which the data to be encrypted is divided into blocks (e.g., 64 or 128 bits) and each block get’s encrypted separately and finally joins.
There are different modes of encryption
ECB (Electronic Code Book)
This is the simplest encryption mode in which we can encrypt blocks parallelly, it is super-fast.
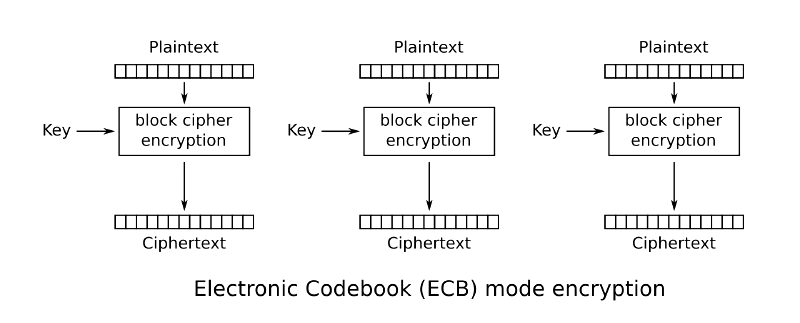
Dis-Advantage:
- If same block of data/text appears more than once, it gets encrypted to the same cipher text.
Example:
Data to be Encrypted
[Block 1] Hello All
[Block 2] Morning Hello
On ECB mode Encryption
[Encrypted Block 1] 9f a6 34 d0 ab 45 91 5e ...
[Encrypted Block 2] 83 22 c4 88 76 39 12 2a ...
[Encrypted Block 3] 9f a6 34 d0 ab 45 91 5e ... ← same as Block 1
-> This might revel some pattern like some data is being repeated.
This will not cause much trouble when encrypting text. But when we are going to encrypt image or videos, it Spoils everything.
Because images have same colour in many places so they are going to get same encrypted result, which sometimes may keep data or
information as such. Image or Videos does not change.
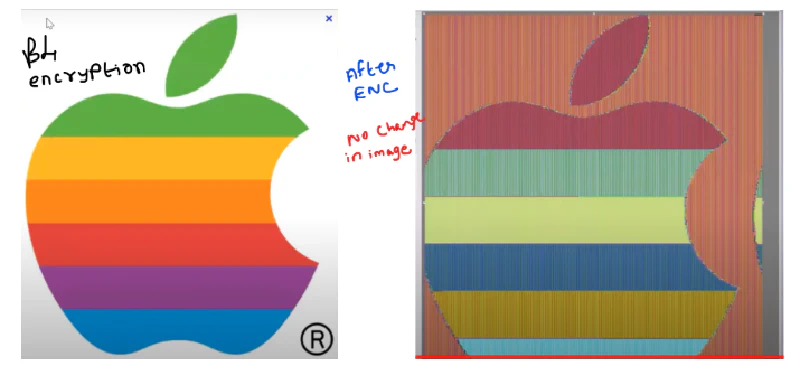
Encrypted but the information is not Lost or not Changed, which is dangerous So how we overcome this.
So here comes
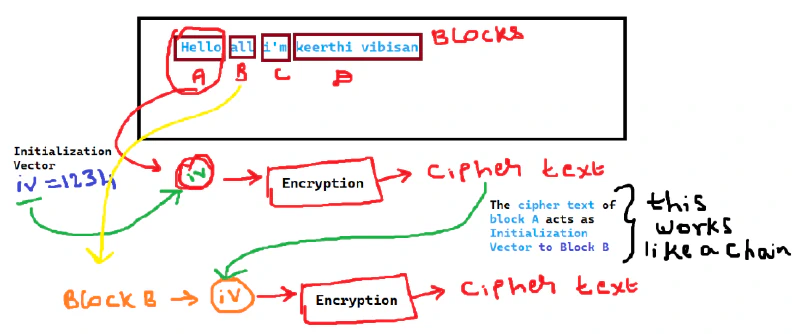
CBC (Cipher-Block Chain)
This is the most used encryption mode, here initially to encrypt we mix the data/text with Initialization Vector (IV) which is a random generated, for next block the previous Cipher data/text acts as Initialization Vector. This ensures no block get same encryption result.
-> when we encrypt image/video with CBC mode

Dis-Advantage:
- No Parallel processing can be done as it is dependent on previous blocks result for encryption.
- Very Slow
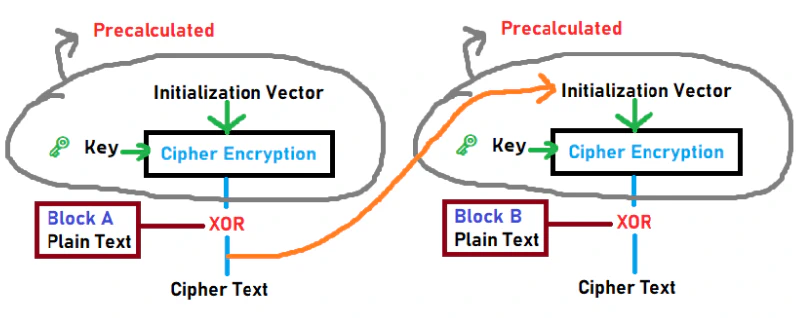
CFB (Cipher Feedback Mode)
This mode is mainly used in Streaming World. This works like CBC, but with a little difference to make it fast (No Parallel Processing).
In this mode we have pre-calculated encryptions for the blocks we just do XOR with the data/text, this is why it is so fast.
Conclusion
We have seen Symmentric Key Encryption and its modes. Now if our data is encrypted and being in-transit. Still people can capture our data packets, but now data is un-understandable. But they can still add more contents to it or delete something on it and much more, which leads to change of data. So still, we need more to Secure It.
