Posted on
in
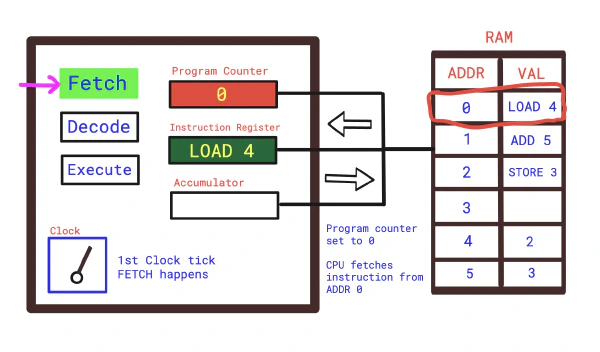
Operating System
• 421 words
• 2 minute read
Tags:
Operating System
Posted on
in
Security
• 373 words
• 2 minute read
Tags:
Security
So i think by turning devices into secure identity, we can make authentication user friendly and secure proof.
Posted on
in
Database
• 1092 words
• 6 minute read
Tags:
Database
Posted on
in
Cryptography
• 798 words
• 4 minute read
Tags:
Cryptography
data's are by default in clear text, when they are stored in RAM or in transit, so anybody who can read RAM or Data packets can get our information, so it is our responsibility to secure it, we cannot stop any one from reading it, but we can make the data un-understandable using encryption techniques.Posted on
in
Cryptography
• 250 words
• 2 minute read
Tags:
Cryptography
Posted on
in
Security
• 788 words
• 4 minute read
Tags:
jwt
Posted on
in
Security
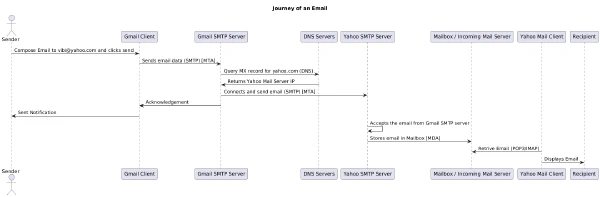
• 953 words
• 5 minute read
Tags:
Email
Posted on
in
IAM
• 297 words
• 2 minute read
Tags:
IAM Basics
It is an authentication method that requires user’s to provide two or more verification factors to gain access to a system or application, rather than relying on one factor or authentication (which is commonly a password).
can combination of password and security question check can be qualified as MFA?
No, having password + security question check will not be qualified as MFA. Because both password and security question belong to the same authentication factor or category.
Posted on
in
Security
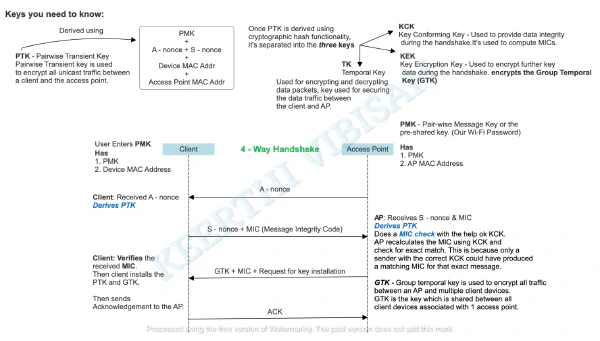
• 780 words
• 4 minute read
Tags:
wifi